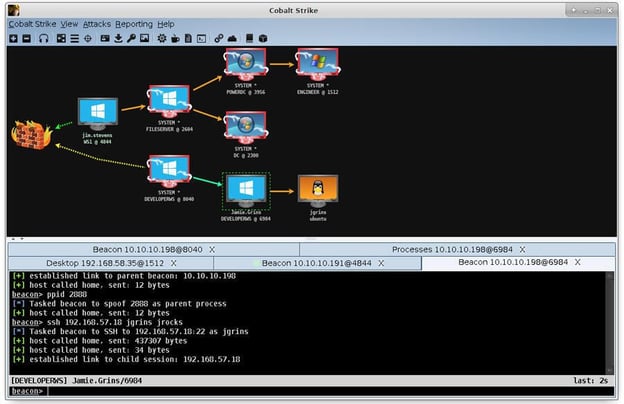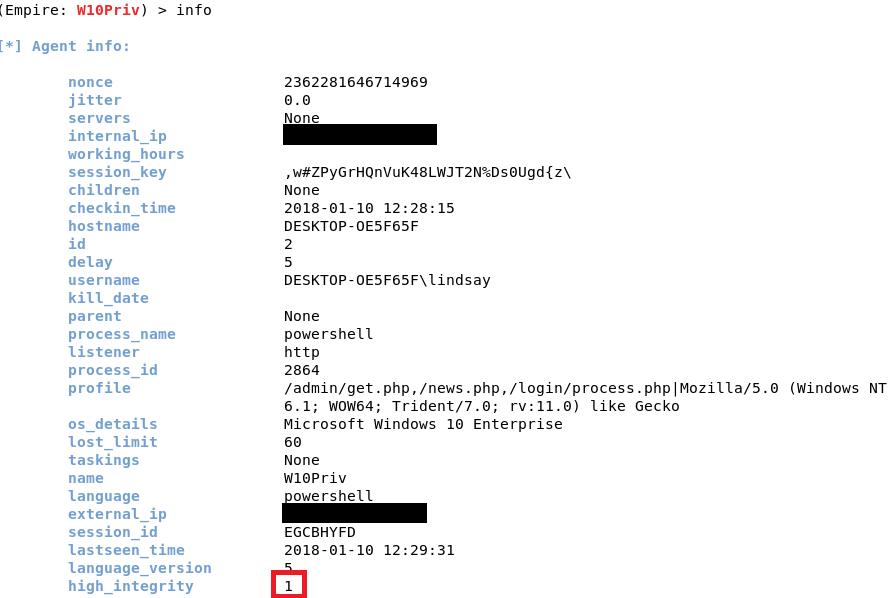
PowerShell Empire Download - Post-Exploitation Hacking Tool - Darknet - Hacking Tools, Hacker News & Cyber Security

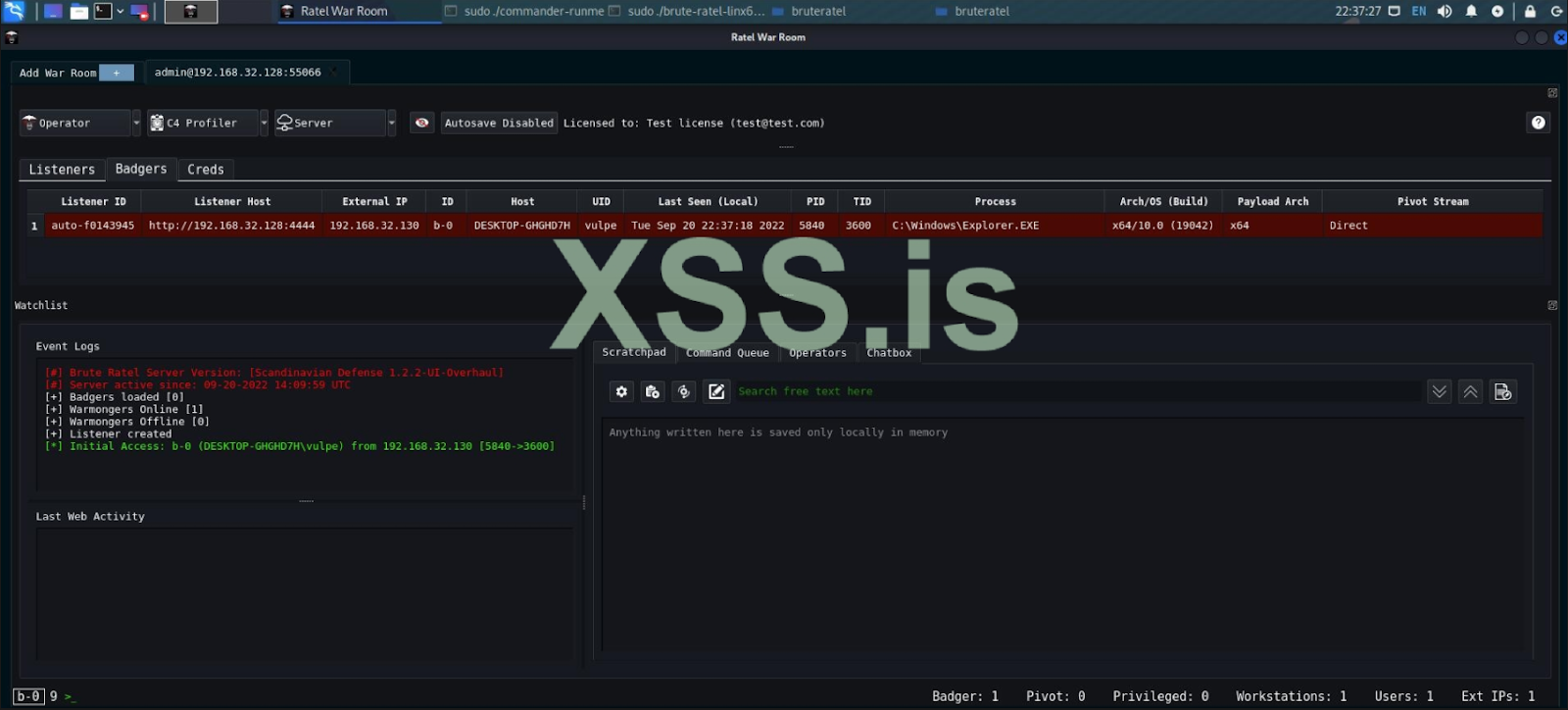
Brute Ratel-Powered Attacks Detection: Post-Exploitation Toolkit Leveraged by Adversaries - SOC Prime

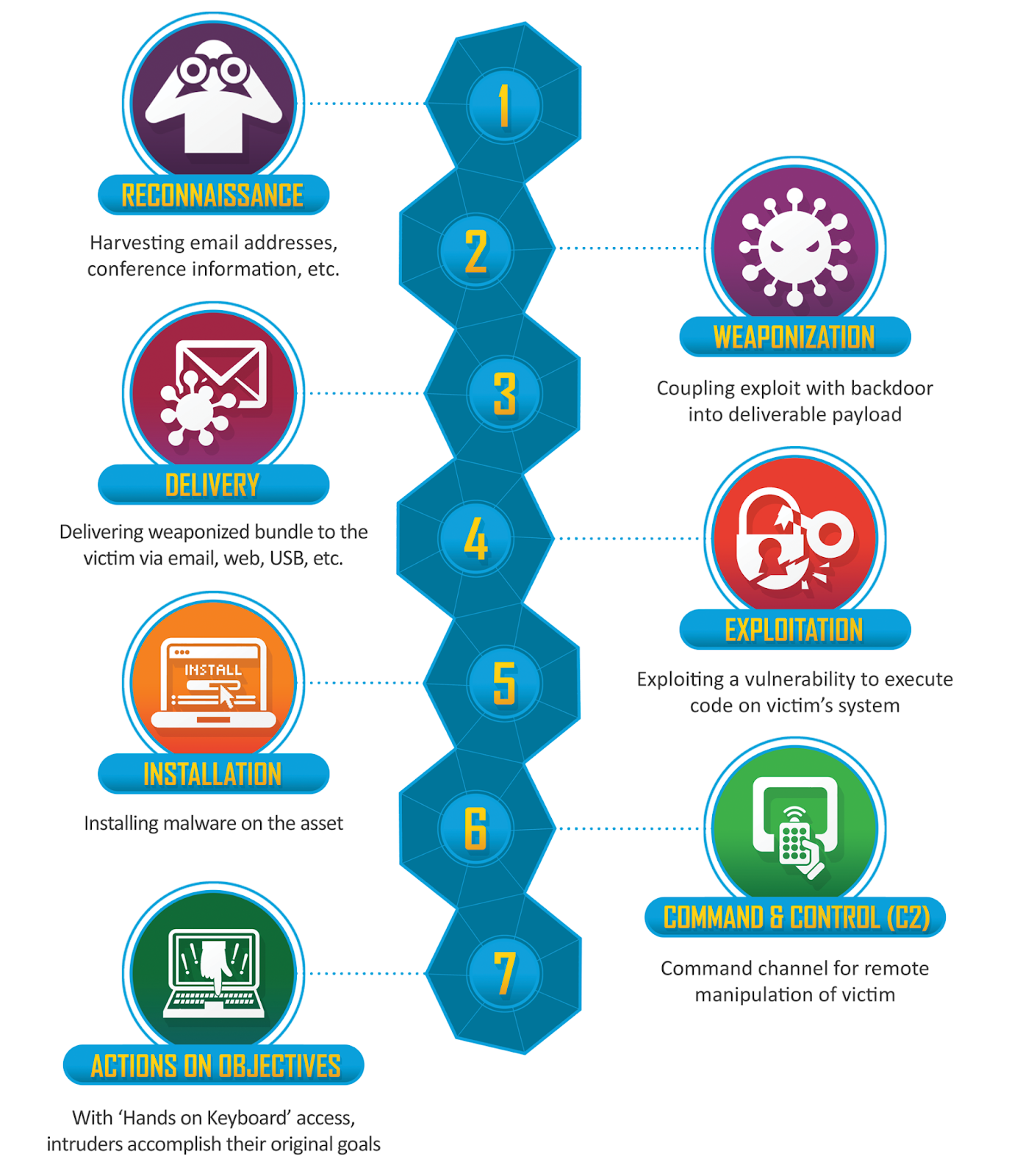
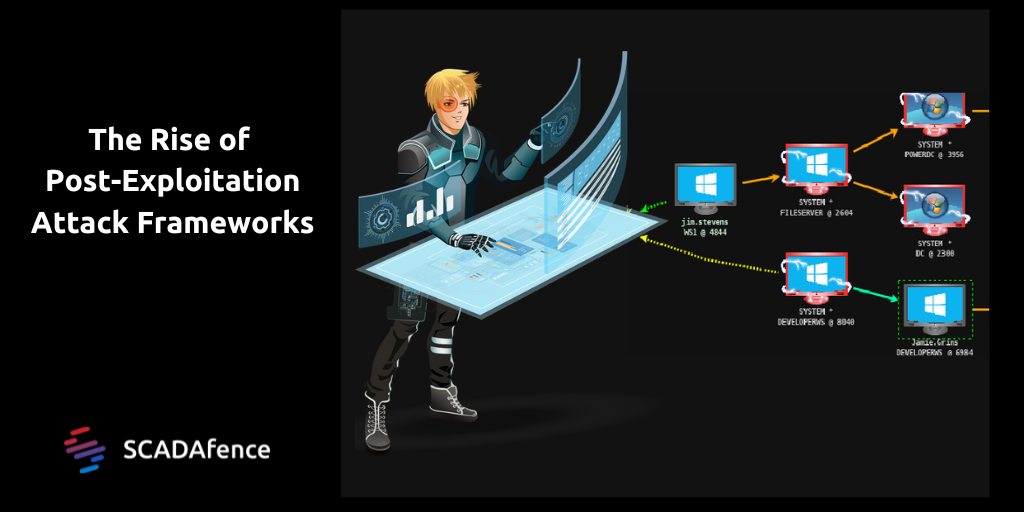
Post-Exploitation Techniques: Maintaining Access, Escalating Privileges, Gathering Credentials, Covering Tracks | Black Hat Ethical Hacking

Florian Roth on X: "mimikittenz post-exploitation powershell tool that extracts plain-text passwords from memory https://t.co/wyIpJH4gWV https://t.co/L2Gi2uN0YV" / X
GitHub - emilyanncr/Windows-Post-Exploitation: Windows post-exploitation tools, resources, techniques and commands to use during post-exploitation phase of penetration test. Contributions are appreciated. Enjoy!

Post-Exploitation Techniques: Maintaining Access, Escalating Privileges, Gathering Credentials, Covering Tracks | Black Hat Ethical Hacking