Drone Hacking and Cyber Warfare: Understanding the Potential Threats to National Security | by 0xSRF | Medium

How Can Drones Be Hacked? The updated list of vulnerable drones & attack tools | by Sander Walters | Medium
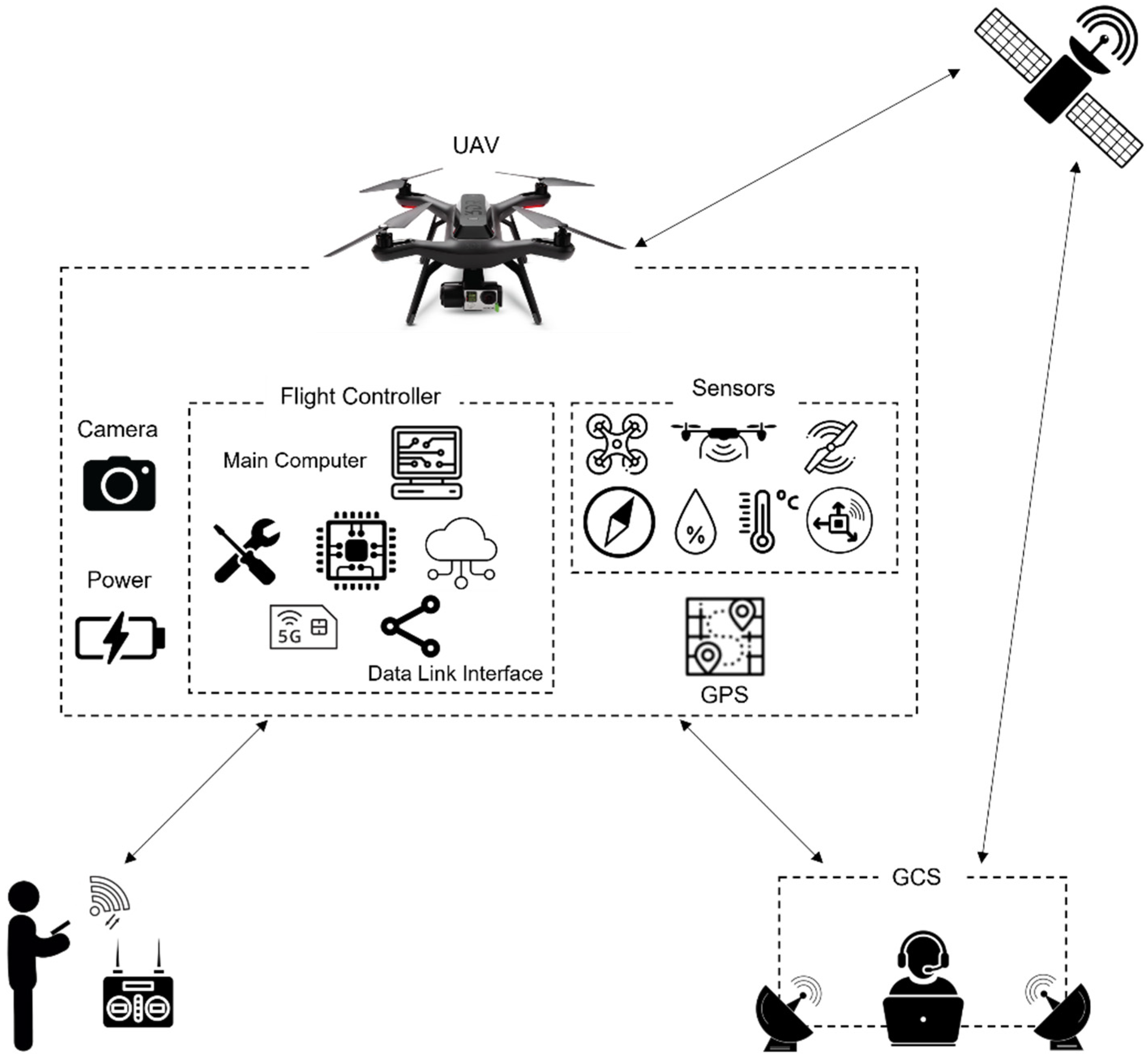
Applied Sciences | Free Full-Text | Drone and Controller Detection and Localization: Trends and Challenges

Sensors | Free Full-Text | An Efficient Authenticated Key Agreement Scheme Supporting Privacy-Preservation for Internet of Drones Communications
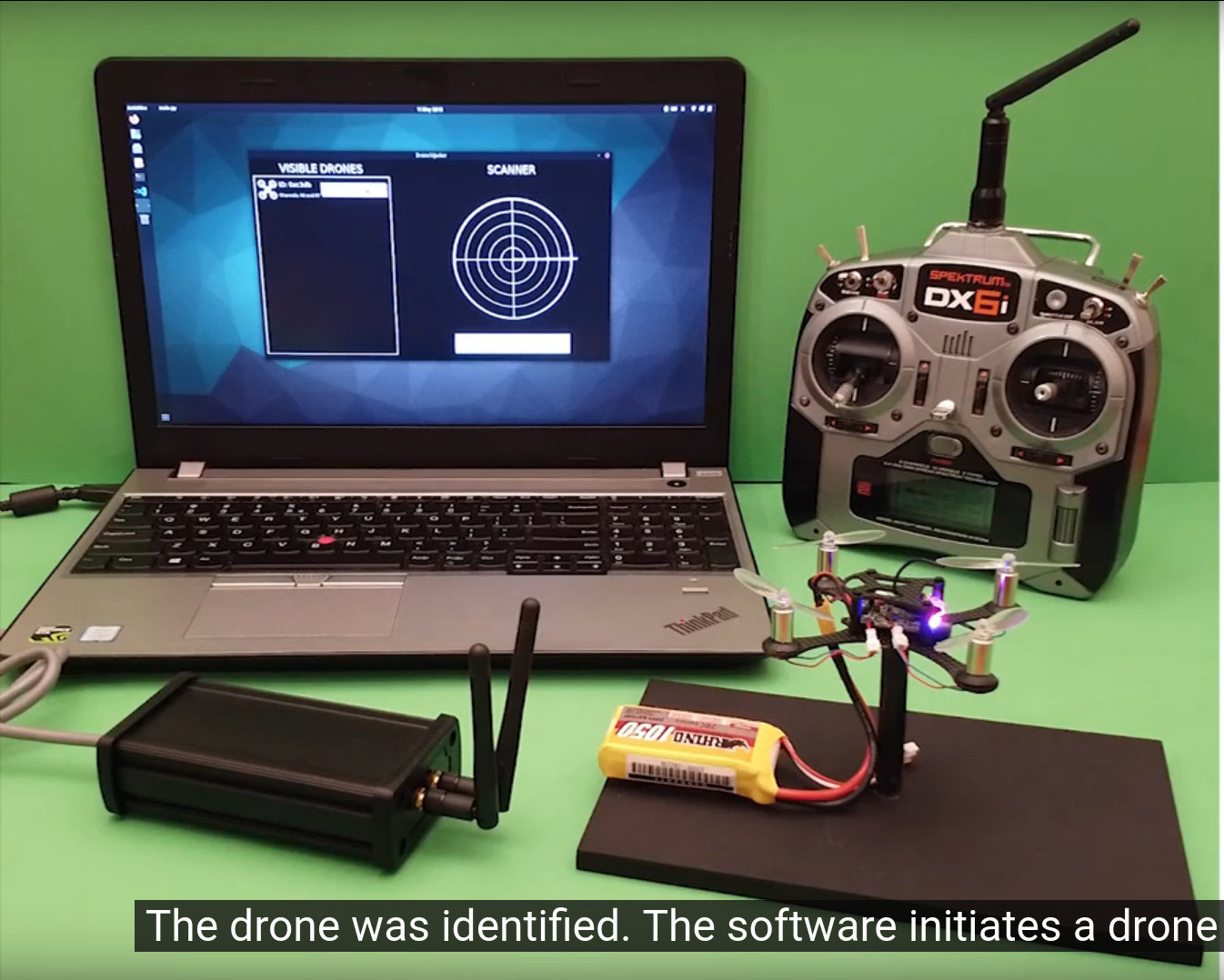
![PDF] Drone Hacking with Raspberry-Pi 3 and WiFi Pineapple: Security and Privacy Threats for the Internet-of-Things | Semantic Scholar PDF] Drone Hacking with Raspberry-Pi 3 and WiFi Pineapple: Security and Privacy Threats for the Internet-of-Things | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a84bd8f41d2225cbf8224963b02d926c196a0b60/5-Figure10-1.png)
PDF] Drone Hacking with Raspberry-Pi 3 and WiFi Pineapple: Security and Privacy Threats for the Internet-of-Things | Semantic Scholar