Learn the Django User Authentication System | by Dane Hillard | Kite — The Smart Programming Tool for Python | Medium
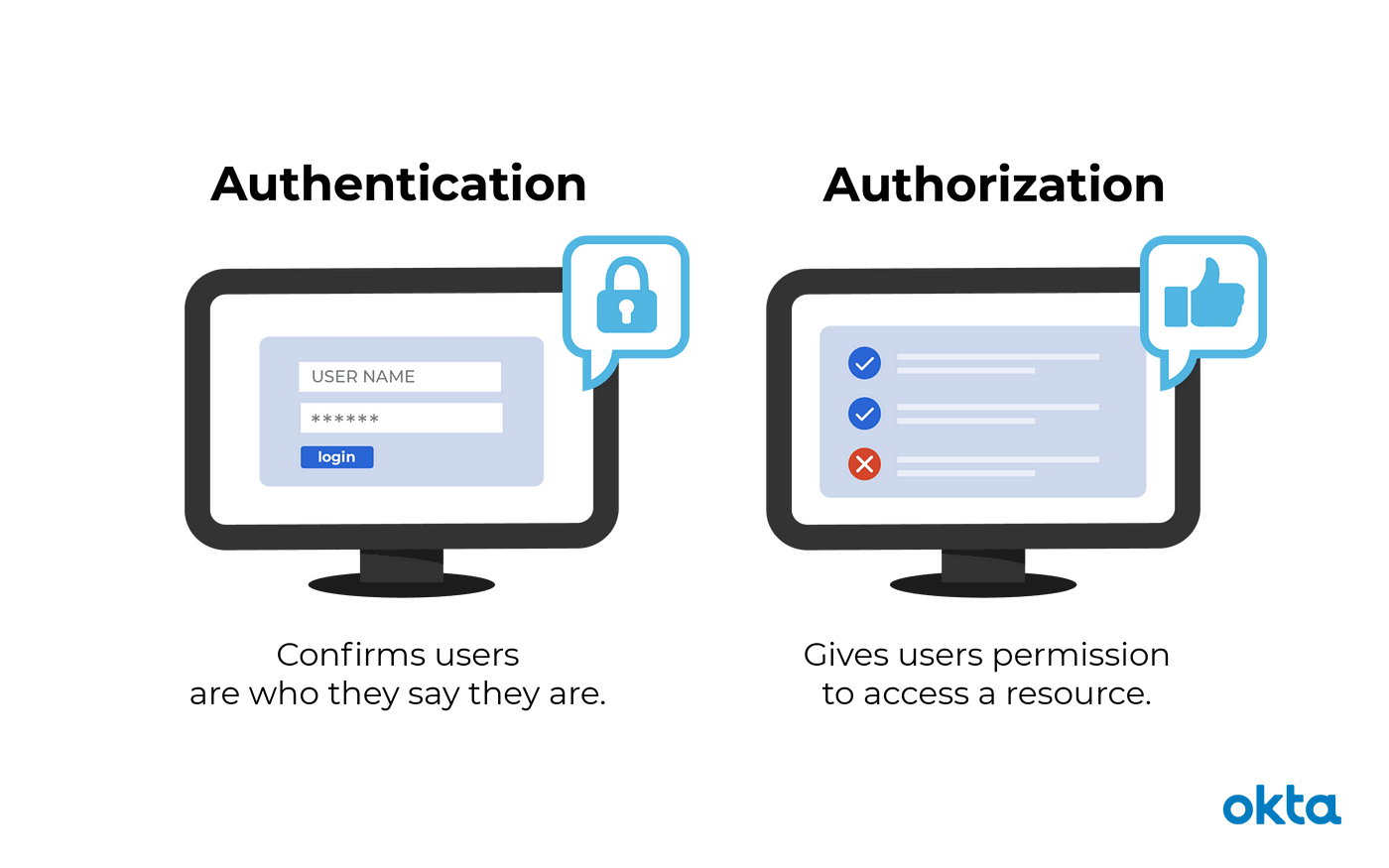
Authentication and Authorization. Visit systemdesign.us for System Design… | by PB | SystemDesign.us Blog | Medium
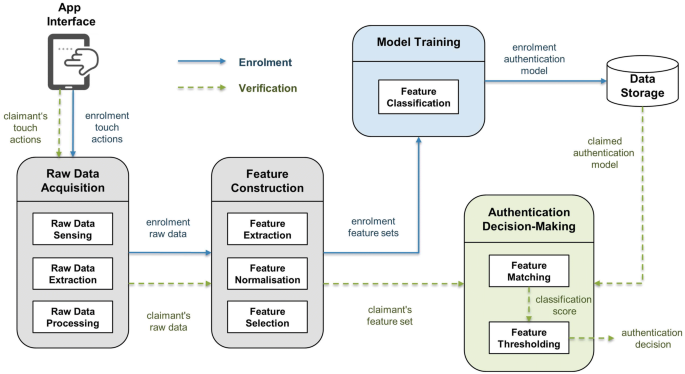
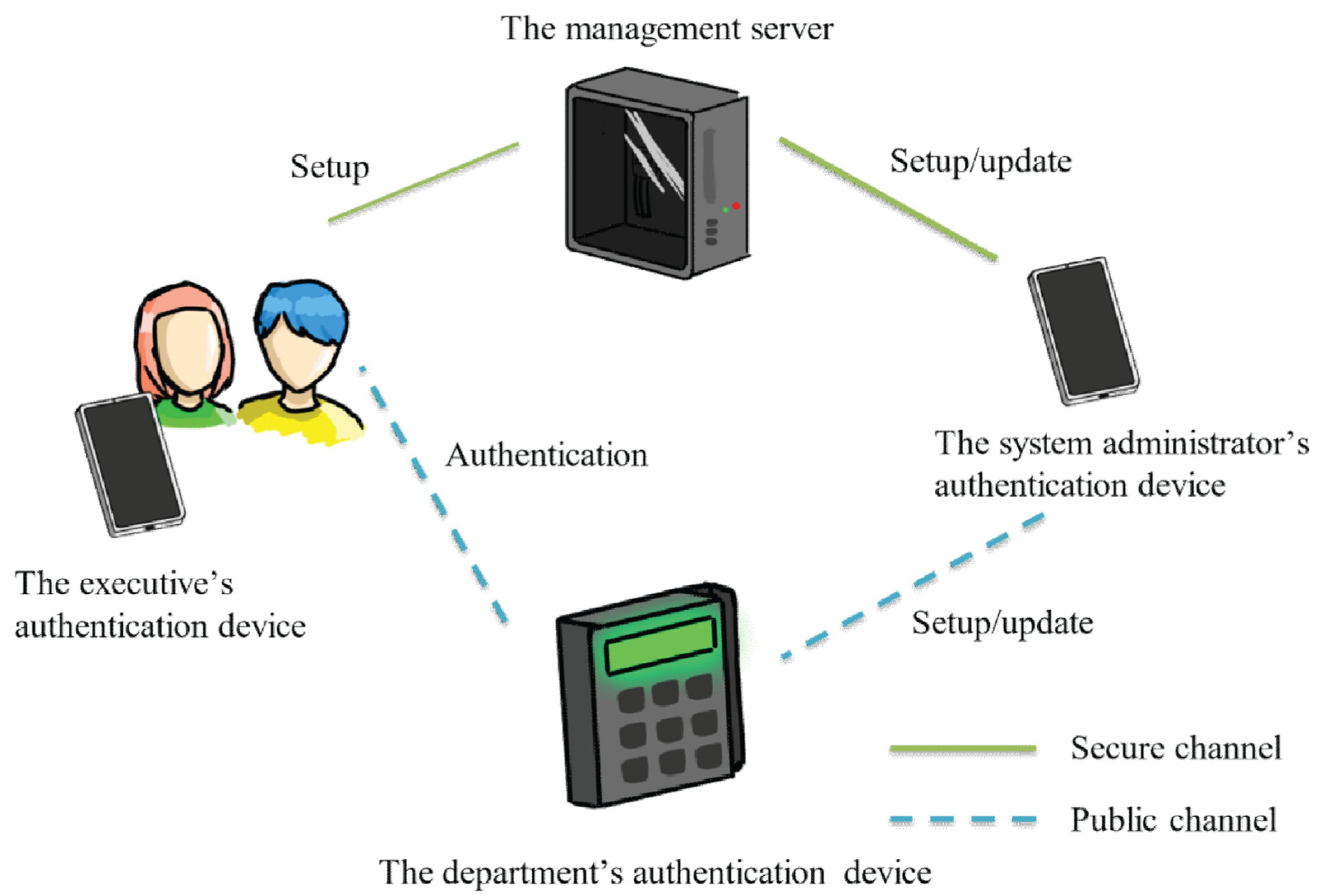
Strengthen user authentication on mobile devices by using user's touch dynamics pattern | Journal of Ambient Intelligence and Humanized Computing
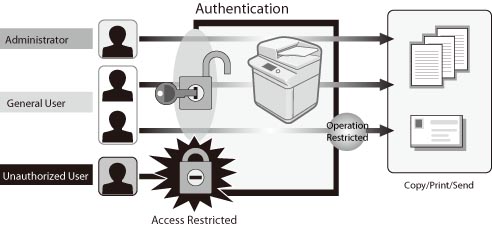
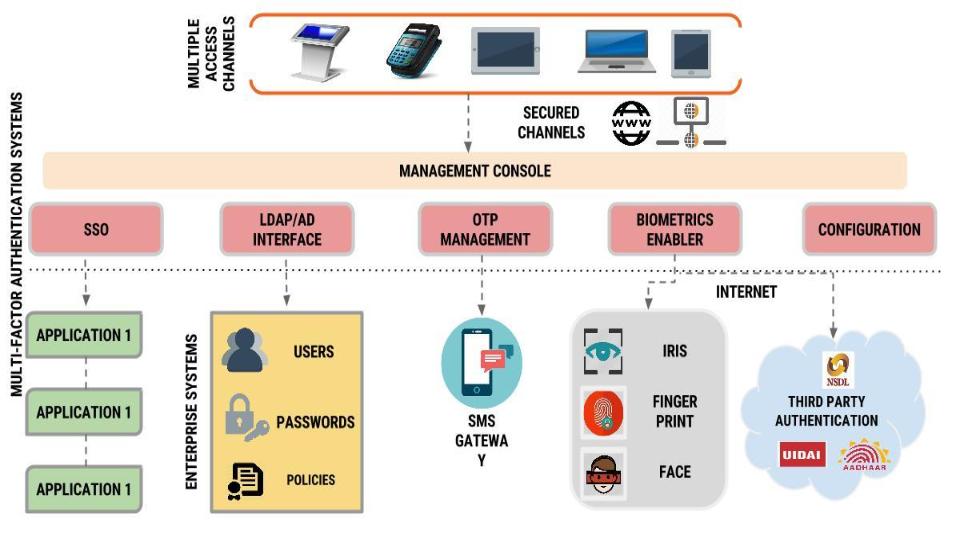
Overview of the Authentication System - Canon - imageRUNNER ADVANCE C3330i C3325i C3320 C3320i - User's Guide (Product Manual)








:max_bytes(150000):strip_icc()/twofactor-authentication-2fa.asp-final-5dc205d2a08b447abfb2e15eb131e28e.png)

.png)